Microsoft Sentinel's Audit Logs: Monitor Activity, Respond to Threats, and Mitigate Risk
Microsoft Sentinel's Audit Log features allow organizations to view and retain activity data within Microsoft 365 and third parties.
Microsoft Sentinel helps organizations meet compliance requirements, investigate threats, and reduce risk for your environment.
____________________________________
Microsoft Sentinel Overview
Microsoft Sentinel is a scalable, Cloud-native solution that delivers intelligent security analytics and threat intelligence for your entire enterprise, powered by AI. Microsoft Sentinel provides a single solution for alert detection, threat visibility, proactive hunting, and threat response, which gives employees time to focus on other prioritized tasks while increasing security. Microsoft Sentinel provides you with a view of threats across your enterprise while alleviating stress from attacks by providing alerts and resolution time frames on security incidents – helping protect your organization by reducing risks.
Traditional security software uses predefined rules to detect threats. While this can be an effective method when applied to known threats, it is not as effective when new types of risks emerge. Microsoft Sentinel uses machine learning to profile users, entities, and the environment, detecting attacks that might not be caught using predefined methodologies. This means you can focus less on sifting through mountains of data and more on relevant and significant incidents.
Audit Logs in Microsoft Sentinel
Audit Logging in Microsoft Sentinel enables organizations to comply more easily with legal standards such as NIST, HIPAA, GDPR, CCPA, and more with its capabilities. Microsoft Sentinel's Audit Logs help your organization respond to security events and compliance obligations by giving you the visibility of your users and admin operations that can be performed in many Microsoft 365 services and solutions. Once the activity is captured, recorded, and retained in your organization's unified audit log, the data can be searched to find the specific activities of users when they open or edit documents and items in a shared space. Administrators who choose to record the activities of users provide visibility into your organization to identify and effectively respond to any suspicious activity that may be taking place – helping you protect your data and mitigate risk for your environment.
Microsoft provides two types of auditing solutions, Basic Audit and Advanced Audit. The Basic Audit is enabled by default for all organizations and provides a record of events that your organization has chosen to audit. When a user or admin performs an audited activity with the Basic Audit, it allows you to log and search for audited activities. This will improve your organization's forensic, IT, compliance, and legal investigations. The Advanced Audit builds on Basic Audit features by providing audit log retention policies, high-value crucial events, higher access to Office 365 Management Activity API, and longer retention of audit records. Depending on the data source, data is retained at no extra cost for 90 days (which can be extended with different pricing options) for detection, investigation, and threat hunting. For storing data long-term, organizations can utilize Azure Data Explorer to store data for up to 100 years by default. Free ingested data types include activity, alerts, and incidents. Additional logging such as intelligent apps, automations, and devices are an additional fee.
Use Cases
As the amount of data flowing in and out of your enterprise grows, and as IT becomes more complex and interrelated, the volume of alerts your security team must deal with can become hard to manage. Unfortunately, a substantial proportion of the alerts generated by security solutions are of little value individually. Using alerts to identify significant issues requires intelligent correlation—a capability built into Microsoft Sentinel. Advanced multistage attack detection minimizes the expertise needed to triage alerts. Multistage attack detection also employs advanced machine learning to accurately identify real threats and minimize false positives by up to 90 percent. Each incident is prioritized to focus security professionals on the most relevant information.
Microsoft Sentinel connects with a number of data sources, including Microsoft 365 and third-party solutions. Depending on the data sources you have connected, you can identify, investigate, and respond to a wide variety of scenarios optimized for your specific needs. Here are some of the most powerful use cases of Microsoft Sentinel Audit Logs:
- Data Theft or Deletion: Reduce your risk of unknown malicious data actions. Actions taken by users that produce a significant change in data files, such as a mass export or data deletion, can be automatically flagged. Once flagged as an incident, your organization can take the appropriate security measures to ensure your data is safe and mitigate the malicious actor.
- Elevating Permissions: Gain a holistic view of permission elevation to reduce the ransomware threat inside your environment. Automatically catch, investigate, and de-escalate the situation before users take damaging actions.
- Risky Sign-In: Increase device and identity security by utilizing risky sign-in flags. Automatically flag when a user signs in on an unregistered / not managed device or from locations that don't make sense. This enables organizations to prevent identity theft and take the appropriate actions to isolate potential threats.
Licensing
Microsoft Sentinel is billed based on the volume of data ingested for analysis in Microsoft Sentinel and stored in the Azure Monitor Log Analytics workspace. Microsoft Sentinel offers a flexible and predictable pricing model. There are two ways to pay for the Microsoft Sentinel service: Capacity Reservations and Pay-As-You-Go.
A capacity reservation has a fixed fee based on a selected tier. Tiers are based on the amount of data (in GB) you estimate will be logged and analyzed in your network every day. The tiers begin with an estimated capacity of 100GB per day. The benefit of this model is a pricing discount when compared to the pay-as-you-go model. With Pay-As-You-Go pricing, you are billed per GB for the volume of data ingested in the Azure Monitor Log Analytics workspace. Typically, if your organization plans on having less than 50GB of data logged daily, the pay-as-you-go model is the better deal. Pricing is also varied by server location.
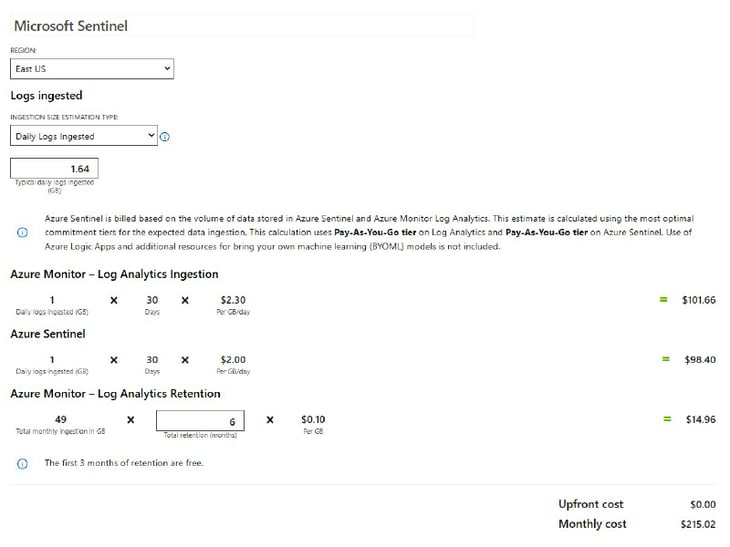
The following is an example of how Azure Sentinel pricing works for an organization that ingests 50 GB a month (1.64 GB daily). This organization has increased retention to six months. While there are several factors that affect pricing, such as connector types, retention, and location, this is an average estimate:
How can Interlink help?
Interlink's Microsoft Sentinel Workshop provides you with the opportunity to better understand all the features of Microsoft Sentinel so that you can gain visibility into your organization and respond effectively to increasingly sophisticated security threats within your organization. This ultimately helps you and your organization to better understand, prioritize, and mitigate potential threats to reduce risk in your environment. For more information on Microsoft Sentinel, pricing optimization, and how Interlink can help your organization, contact us today for questions!
Steven Braunschweiger
Steven Braunschweiger is a Senior Enterprise Architect at Interlink. Steven is a talented IT Architect and Technical Leader for over 20 years and has assisted companies in transforming their Hybrid Cloud Solutions. With multiple certifications in Azure Solutions, Steven is a key member of the Interlink team, here providing technical expertise to clients, and in helping our team implement and driving ongoing best practice development in our service delivery.


